Network security typically invokes the image of barriers and firewalls protecting the internal network from the outside world. The network stays cloistered away and security is an epic battle fought at the fronts. This image is long dead in the post-security world.
Security has become a ship riding through a violent sea. The hull should be strong, but the inside should be made to handle some degree of failure. Flat networks may be fashionable, but they have their risks.
Network Topologies
Network topology defines the way a networked is structured. It describes the network’s layout and how each piece of the network talks to each other piece, if at all. Despite the fact that network topologies can get complicated with terms like: Bus Topology, Star Topology, Ring Topology, Tree Topology, Mesh Topology, and Hybrid Topology, a lot of information about network topology is tailored towards the logical side (making it all work). All you really need to start from a security perspective is to know the difference between a Flat Network and a Segmented Network (sometimes also called a Routed Network). Pretty much all of the action happens at the network layer.
Flat Networks
Flat networks have become common for small businesses (and ironically enough certain development shops). They’re called “flat networks” because they’re like a flat topology map. There is no high or low, nothing is harder or easier to access from any point in the network. Everything can easily see and talk to everything else. See Figure 1 for an example of a flat network at a common small business.
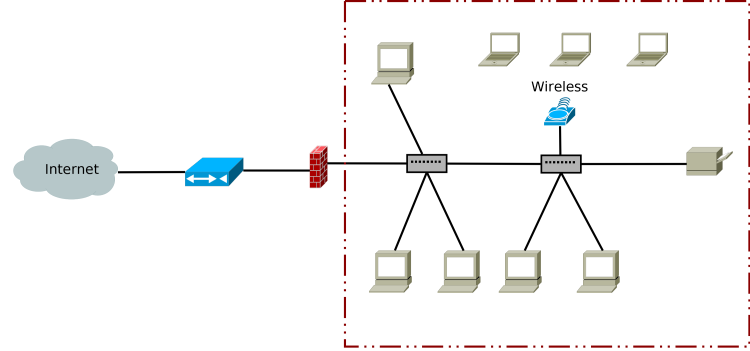
This is common with most home setups, and a depressing number of small businesses. Traffic goes from the internet, to a modem, then passes through the firewall which is the only “gate” protecting our network. Inside we hit a router and whatever switches or other networking hardware connects everything. There’s probably a wireless network which both guests and employees connect to. Everything can access everything else.
At this point we are relying on nothing internal being trustworthy and our network never being breached. In the days of BYOD and more and more internet connected devices, we are essentially placing our trust in both never being invaded and never being betrayed. Flat networks work in certain scenarios, but not in security.
Segmented Networks
Most newer consumer grade routers come with the option for a guest network. The guest network which blocks the one WiFi channel from the rest of the network is the first step in setting up a segmented network. A segmented, or routed network is a network with a nontrivial topology which restricts connections between different nodes on the network.
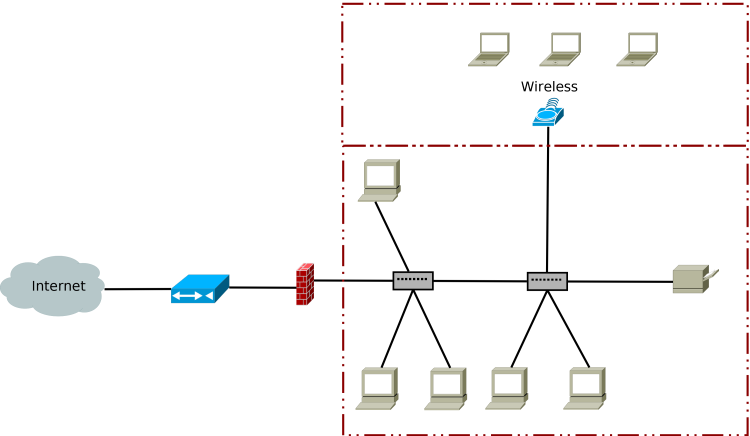
Despite this being a near trivial example which is available in pretty much any mid-grade consumer router from the past 5 years, this creates a massive improvement in security, but adds a caveat. If you connect to the wrong access point, you can’t communicate with the internal network at all (and this happens to users a lot), but neither can a compromised machine or a malicious actor. You have segmented the network and traffic is routed so that it cannot communicate with something it shouldn’t be able to.
Network Topology and Security

Network topology impacts security as well as security response. The more segmented the network, the harder it is to breach internally and the harder it is for a breach to spread. A hard hull on a ship is great, but you want rooms which seal inside in case of a breach. Too small of a room or too many rooms and your ship is impractical for cargo or even travel.
You can’t just block every device from every other device in a business (or even most home environments). Devices need to communicate. That’s the beauty of routing though, you can route traffic from certain sources to other sources. You can control what a server exposes to a different part of the network via NAT or other techniques.
The topology can impact specific security ingresses as well as how a response situation happens. You may fail to stop a machine from getting new generation malware, but you can limit its ability to spread and give yourself time to notice. Modern security isn’t about 100% prevention, it’s about the damage control and recovery. The dream of perfect security has long since sailed.
Mitigation Techniques
Basic routing and segmentation can obviously slow down many attacks and make others impractical, but newer generation security includes things like internal QoS style directional throttling, internal port blocking, and jumpboxes. Sometimes you want a firewall on an internal part of the network. Other times, you want all your Internet of Things or other embedded devices separated for privacy and security.
Some companies treat each site like they’re just some other organization with limited access. Some do this internally between departments, or even teams. It requires heavily investing in network equipment to be practical, but when the zero-day ransomware of the month makes its rounds, the places with the seemingly paranoid security don’t call. They trade convenience for security, and if they get hit, it’s usually a machine or two at most because the infection is localized and quarantined quickly. Since they’re willing to throw money at security, they’re usually also willing to throw money at backups, so the whole ordeal is just an inconvenience at most.
Assessing Risk and Practicality
There isn’t a one size fits all approach to network security. You have to know what’s on the network and what needs to communicate with what for the business to function. If you don’t even know what’s there, how do you even begin to secure it without breaking everything?
If you want to secure a network, you need to consider how important a given piece of equipment is from both a security standpoint and a functionality standpoint. What is the biggest threat to your security and to your business? Those fancy workstations may be expensive, but that old file server in the closet has years of work on it. Do you let just anyone have access? If something runs the credit card system, can you afford for it to go down or be inaccessible? These types of systems need to be more segmented from the machines that don’t really matter.
Should the random employee in accounting be able to hit the developer file server? Should the random developer have access to the accounting RDP? Probably not, but a lot of networks treat all employees as trustworthy in the network. We don’t necessarily distrust them, we distrust what can happen to their devices. It takes one bad email and a minor lapse in security to watch a site succumb to ransomware machine by machine.
Sometimes the whole workflow needs to be reworked to make network security practical. If everything is on one file server, what happens if it goes down or is compromised? You can make this shared between segments with proper routing, but sometimes it’s best to split the server into smaller servers so each segment has its own share. Then, you don’t need to mess with the routing and it’s much easier to segment the network.
Application
There needs to be a balance between security or functionality, and this schism gets even more obvious when equipment budgets are limited. You can potentially throw money at the problem, but if you don’t have the cash, your options are limited. Cheaper equipment might be able to do the security part, but you usually feel it in either latency, throughput, or device count.
Network topology heavily impacts security and security mitigation. Flat networks are easy to access and work with for both you and a threat actor. Segmented networks can mitigate this, but can impact normal operations. There must be a balance and an understanding of what needs to talk to what. Sometimes, the whole network needs to be redone with security in mind.
There are costs to every security decision, but basic segmentation is cheap, easy and practical. As long as you don’t go overboard, there won’t be much impact on functionality for employees, but there will be a huge impact on an attack. More advanced segmentation requires better quality equipment (or better usage of existing equipment depending), and internal process adjustment (and training).
Featured image by Eddy Blondey from Pixabay

